New Wave of GoBruteforcer Attacks
A recent surge of GoBruteforcer attacks has focused on databases belonging to cryptocurrency and blockchain projects. This tactic aims to integrate these databases into a botnet capable of brute-forcing user passwords for services like FTP, MySQL, PostgreSQL, and phpMyAdmin on Linux servers.
Motivating Factors for the Attacks
According to Check Point Research, this recent wave is fueled by two main factors: the widespread reuse of AI-generated server deployment templates that often utilize common usernames and weak default settings, along with the ongoing presence of legacy web stacks such as XAMPP, which expose FTP and admin interfaces with minimal security measures.
Technical Overview of GoBruteforcer
First documented by Palo Alto Networks Unit 42 in March 2023, GoBruteforcer, also referred to as GoBrut, can target Unix-like platforms across x86, x64, and ARM architectures. It establishes an Internet Relay Chat (IRC) bot and web shell for remote access, while also deploying a brute-force module to identify vulnerable systems and expand its botnet capabilities.
The Evolution of the Malware
A follow-up report from Lumen Technologies’ Black Lotus Labs in September 2025 revealed that some infected bots controlled by another malware family, SystemBC, were also part of the GoBruteforcer botnet.
Advancements in the Malware
Check Point noted the emergence of a more advanced version of this Golang malware by mid-2025, featuring a heavily obscured IRC bot, enhanced persistence methods, process-masking techniques, and dynamic credential lists. These lists included frequently used usernames and passwords that facilitate remote logins, drawing from commonly used names found in database tutorials and vendor documentation.
Attack Strategies and Targeting Techniques
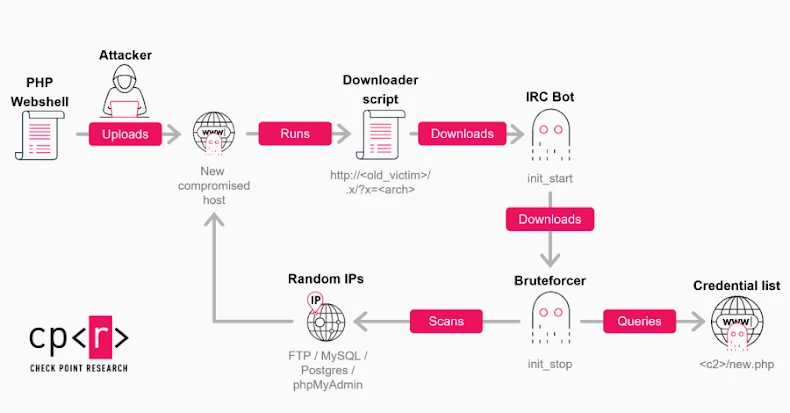
In these campaigns, Check Point observed that internet-exposed FTP services on XAMPP servers are exploited to upload a PHP web shell. This web shell, in turn, downloads and executes an updated version of the IRC bot using a shell script, based on the system’s architecture. Once a host is compromised, it can serve multiple functions, including running brute-force attempts on various services, hosting payloads for other compromised systems, or acting as a backup command-and-control (C2) node.
Wider Implications of the Attacks
The research also uncovered that compromised hosts were used to query TRON blockchain addresses via the tronscanapi[.]com service, targeting accounts with non-zero balances, which indicates a focused effort on blockchain projects. Check Point summarized that GoBruteforcer illustrates a persistent issue tied to exposed infrastructure and weak credentials, which are exacerbated by automated tools, allowing the operators to exploit numerous misconfigured services.